
Navigating the Cybersecurity Landscape with NIST’s Updated Framework
Organizations are recognizing the critical importance of robust cybersecurity measures. The National Institute of Standards and Technology's (NIST) recent update to its Cybersecurity Framework (CSF) to Version 2.0 is a ...

The Evolution of IT Support: From Reactive to Proactive Models
Businesses today are changing how they handle technology. Instead of waiting for problems to happen, they're getting ahead of them. This shift from waiting-and-fixing IT to proactive planning is a ...

Why Your MSP Should Have SOC 2 Compliance: Securing Your Digital Trust
In an era where data security is paramount, the choice of a Managed Service Provider (MSP) hinges on their ability to safeguard sensitive information for their clients. This is where ...

Navigating the Rising Tide of Cyber Attacks: Insights for Small and Medium-Sized Businesses
As we look back on 2023, the surge in cyber attacks has emerged as a formidable challenge, particularly for small and medium-sized businesses (SMBs). With limited resources and often less ...

Staying Ahead of the Curve: Top Compliance Strategies for Financial Advisors
The landscape of financial compliance is ever-changing, with 2023 presenting a fresh set of challenges for financial advisors. As regulations evolve and technology advances, staying on top of compliance requirements ...

Fortifying Data Compliance Amid Financial Flux: Strategic Approaches for IT Security in Uncertain Times
Having a robust IT Compliance Strategy is crucial for 2024. The financial tremors of 2022 have left an indelible mark on the operational outlook in the coming new year. With ...

AI Implementation in Healthcare to Enhance Patient Care and Data Management
AI Implementation in Healthcare has ushered in a transformative era, where the integration of Artificial Intelligence (AI) is not merely an innovation but a necessity to enhance patient care and optimize ...

The Role of Regulatory Compliance in Life Sciences
As we navigate the new age of AI, the nexus between cybersecurity and regulatory compliance has deepened, particularly in the Life Sciences and Professional Services industries. As owners of vast ...

Financial Data Protection: Decoding the Cybersecurity Challenges in 2023
For cybercriminals around the world, the vast array of sensitive financial data presents an attractive target. The inherent vulnerabilities of the financial sector are accentuated by high-stakes operations, a high ...

AI-Driven Cyber Threats: A Guide for C-Suite Executives and IT Managers
AI-driven cyber threats are not just a fact; they are an ever-evolving issue for many industries. In the span of three years, Artificial Intelligence (AI) has evolved from a budding ...

Protecting Your Assets: Lessons from the MGM & Caesar’s Recent Cyberattack
In our rapidly evolving digital landscape, the significance of airtight cybersecurity is paramount. The recent incidents at MGM & Caesar's highlight this urgency. The Incident MGM faced operational hiccups when ...

23 Signs Your Business Needs Outsourced IT
Technology is the backbone of virtually every business operation, IT challenges can significantly hinder growth and productivity. From frequent downtime to cybersecurity threats, these issues pose serious risks that can ...

Benefits of Managed IT Services: Why Use a Managed Service Provider
In today's fast-paced business environment, organizations face countless challenges when managing their IT infrastructure. As technology evolves and companies scale, businesses need flexible, secure, and efficient IT to stay ahead ...

What is Third-Party Risk Management?
As business operations become increasingly complex and interconnected, third-party risk management (TPRM) is no longer optional. [ez-toc] You Are Only as Safe as Your Vendors Companies rely heavily on third-party ...

Cost of Cyber Attacks: One Company’s Worst-Case Scenario
Cyber attacks are becoming increasingly common, and cybercriminals see small to medium-sized businesses as prime targets. The devastating consequences of a cyber attack can be long-lasting and far-reaching, as demonstrated ...

RIA Cybersecurity: Prepare for New SEC Cybersecurity Requirements (2023)
Last year the Securities and Exchange Commission (SEC) voted to implement new and amended SEC RIA requirements to the Advisers Act of 1940 for cybersecurity risk management for registered investment ...
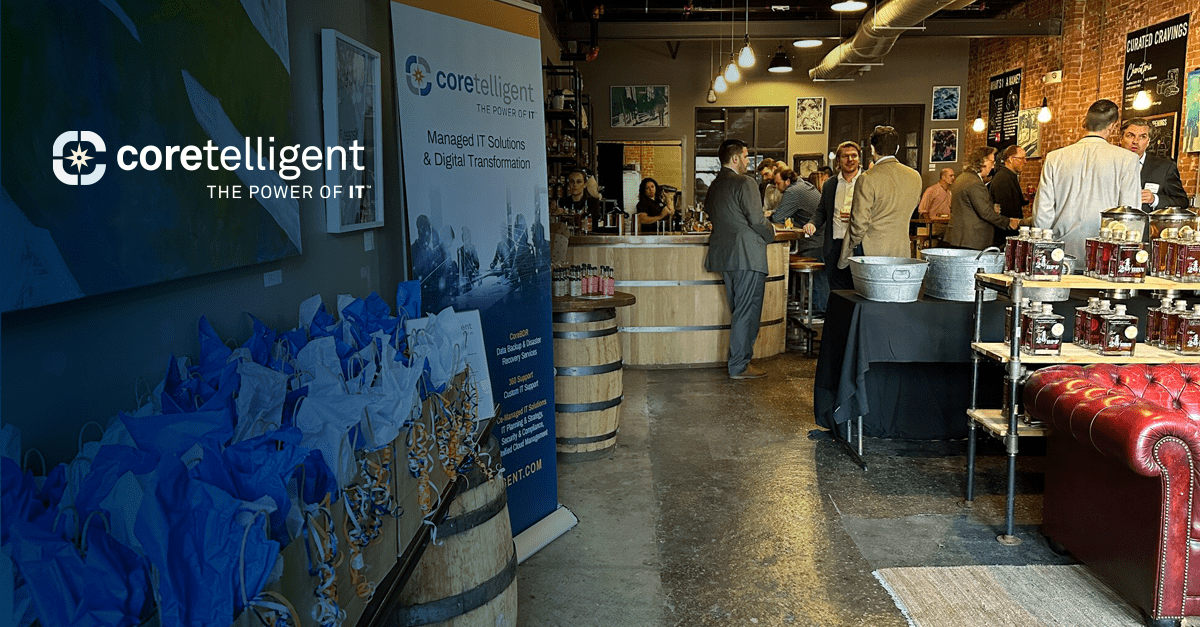
Coretelligent Hosts CoreDTS Mixer at Craft Distillery
Connecting with others in the business world has the apparent benefits of expanding your network, gaining valuable insights, and sharing your business with others. But when it's done correctly, networking ...
Security vs. Compliance: Differences & Similarities (2023)
Security and compliance are often used interchangeably in IT, but that is actually a misnomer as they are not equivalent. So, just what are the differences between security vs. compliance? ...

Breach Detection: Could You Detect a Data Breach?
With the increasing reliance on technology in today's business world, the risk of data breaches is at an all-time high, making breach detection a crucial factor in protecting sensitive data ...
10 Tips to Better Spot Phishing Emails
Email phishing activity is reaching a new high, especially in the financial services sector. Common attacks are nothing more than online scams involving gift cards, while some are targeted spear ...


