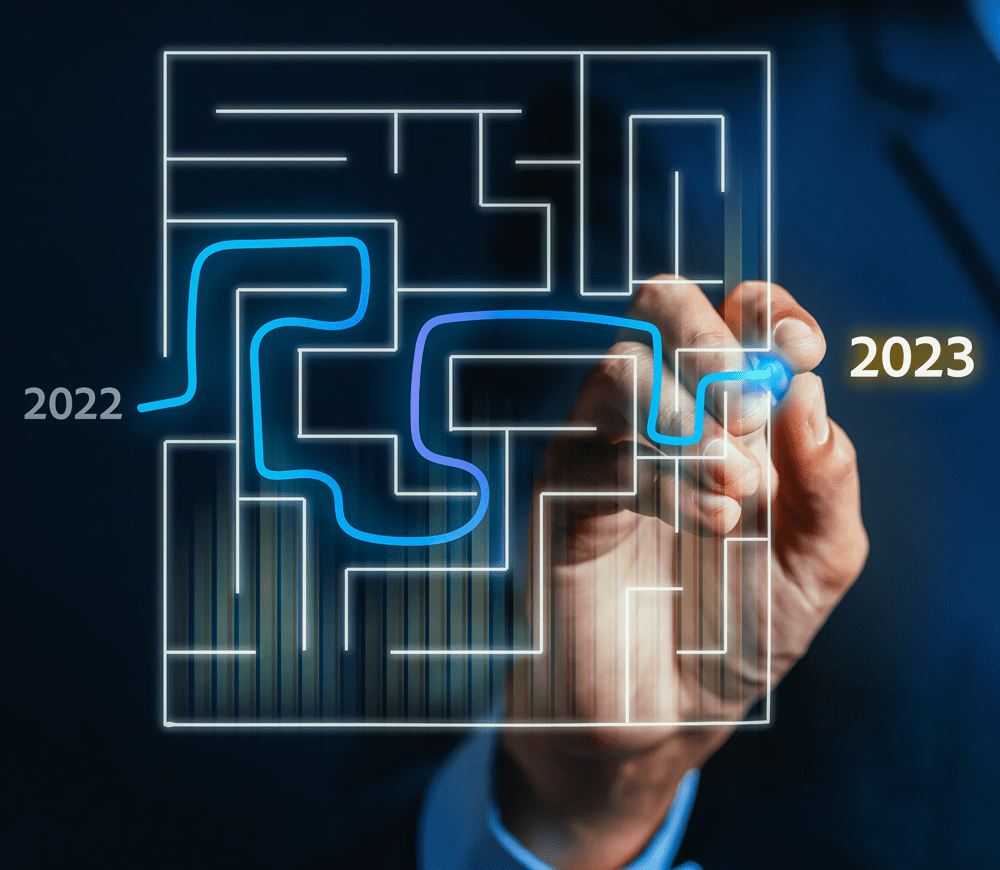
 As we move into the last quarter of the year, it’s time for the annual review and realignment of your IT planning and strategy. Of course, you have actively been implementing your IT roadmap throughout the year, but a year-end IT planning and review is an opportunity to evaluate its effectiveness and update it for the upcoming year. Here are some things to keep in mind as you plan for the end of the year.
As we move into the last quarter of the year, it’s time for the annual review and realignment of your IT planning and strategy. Of course, you have actively been implementing your IT roadmap throughout the year, but a year-end IT planning and review is an opportunity to evaluate its effectiveness and update it for the upcoming year. Here are some things to keep in mind as you plan for the end of the year.
Year-End IT Planning and the IT Road Map
An IT roadmap is a strategic plan that outlines how your business will use technology to achieve its goals. A well-planned roadmap can help your business scale, improve ROI, reduce risk, and increase productivity.
Utilizing an IT roadmap ensures that your IT investments drive value and growth. In addition, a comprehensive plan can help identify areas of your organization’s IT infrastructure that need improvement and prioritize addressing them.
As with any plan, a strategic IT roadmap is only effective if you use it. A high-level annual review offers an opportunity to evaluate successful goal completion, realign with business goals, re-examine key initiatives, acknowledge and implement a plan for gaps, and provide valuable data for setting future KPIs.
What Should a Year-End Review Encompass?
As with other company activities, the year-end technology review reflects what you put into it. So don’t regard it as a meaningless exercise; instead, see it as an opportunity to get valuable information about your company. While results vary from firm to firm, there are certain aspects that all year-end reviews have in common.
1. Review the Current Technology Roadmap
Appraise the initiatives, tactics, and timelines of the current IT strategic plan to evaluate successful completion and future updates.
Reassess the technology of the organization, including:
- Cybersecurity practices and policies
- Technology infrastructure
- Cloud storage and applications
- Processes and data governance
- Due diligence, compliance requirements, and risk management
2. Review Business Goals
The review process should also start with refreshing yourself with your company’s mission, vision, and values. Then, this is an opportunity to assess business functions and realign with these foundational pillars.
Of course, a review would not be complete without the inclusion of the business goals for the year you are looking back over. These business objectives can help you formulate a list of questions that can be answered through your review.
Review current business objectives, initiatives, and IT needs across the organization to determine IT initiatives. SWOT analysis can help identify gaps in IT needs across the organization. Key elements to include in the plan include proactive cybersecurity, compliance requirements, business drivers, expected growth, risk management, and identifying opportunities.
3. Assess Key Performance Indicators and Results
Determining success by reviewing metrics is key to establishing the effectiveness of any plan, and an IT roadmap is no exception. Beyond assessing whether goals were completed, there’s also plenty of insight to be gleaned from evaluating the objectives you did not reach. Undergoing this exercise is where the work of developing next year’s IT roadmap through identifying gaps and deficiencies, goals out of alignment, and new technology needs begins.
4. Putting IT All Together for Next Year
The outcome of this exercise is to use these findings from this strategic year-end IT planning process to set initiatives and develop strategic goals for your organization for the upcoming year.
Additionally, business leaders should look externally and evaluate business drivers and market forces, apply competitive research, and assess technology disruptors when determining upcoming IT priorities and business goals to include in next year’s plan.
Download our e-book Paving the Road to Success with Strategic IT Planning to learn more about how developing and implementing an IT roadmap can steer your firm towards success.
 About Chris
About Chris
As Chief Technology Officer at Coretelligent, Chris Messer is a transformational and strategic IT leader who establishes and leads Coretelligent’s technical vision and technological development. Click here to learn more about Chris.

 The way we interact with technology has undergone a permanent change.
The way we interact with technology has undergone a permanent change. 
 Cybersecurity Awareness Month is recognized every October. Now in its 19th year, this month is a collaborative effort between
Cybersecurity Awareness Month is recognized every October. Now in its 19th year, this month is a collaborative effort between 
 Businesses invest in many technologies to prevent cybercriminals from breaching their systems. By implementing firewalls, antivirus, and endpoint protection, organizations hope to put a barrier between an attacker and company data. These tools are very effective when implemented correctly, but there’s a catch. Cybercriminals often bypass perimeter security measures by focusing their efforts on one thing, humans.
Businesses invest in many technologies to prevent cybercriminals from breaching their systems. By implementing firewalls, antivirus, and endpoint protection, organizations hope to put a barrier between an attacker and company data. These tools are very effective when implemented correctly, but there’s a catch. Cybercriminals often bypass perimeter security measures by focusing their efforts on one thing, humans.



 Our shift to a digital world is fueling the creation of massive data reservoirs with almost unlimited potential. With this increase comes new data terms and technologies for managing and analyzing data. This digital transformation shift can result in companies generating more data than they can manage or utilize with their current infrastructure and resources if not adequately conceptualized.
Our shift to a digital world is fueling the creation of massive data reservoirs with almost unlimited potential. With this increase comes new data terms and technologies for managing and analyzing data. This digital transformation shift can result in companies generating more data than they can manage or utilize with their current infrastructure and resources if not adequately conceptualized.

 About Chris
About Chris


 The heads of the
The heads of the 
