Earlier this month, the U.S. Senate unanimously passed a major piece of cybersecurity legislation. It requires companies in key sectors identified as critical infrastructure to report significant cyberattacks to the government within 72 hours. The legislation will have far-reaching impacts across most sectors.
The introduction of the Strengthening American Cybersecurity Act of 2022 comes as federal officials broadcast the likelihood of strengthening cybersecurity requirements as a national security response. The escalating conflict in Ukraine has only increased concerns that the United States could be the target of Russian cyberattacks.
Sen. Gary Peters of Michigan, the co-author of the bills, said: “As our nation continues to support Ukraine, we must ready ourselves for retaliatory cyber-attacks from the Russian government.”
The legislation, which still must pass the House, would require critical infrastructure owners and civilian federal agencies to report to the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours if they experience a cyberattack.
Several members of the U.S. House of Representatives, including Yvette Clarke and John Katko, both of New York, are working with Peters and Senator Rob Portman of Ohio to pass the bill in the House.
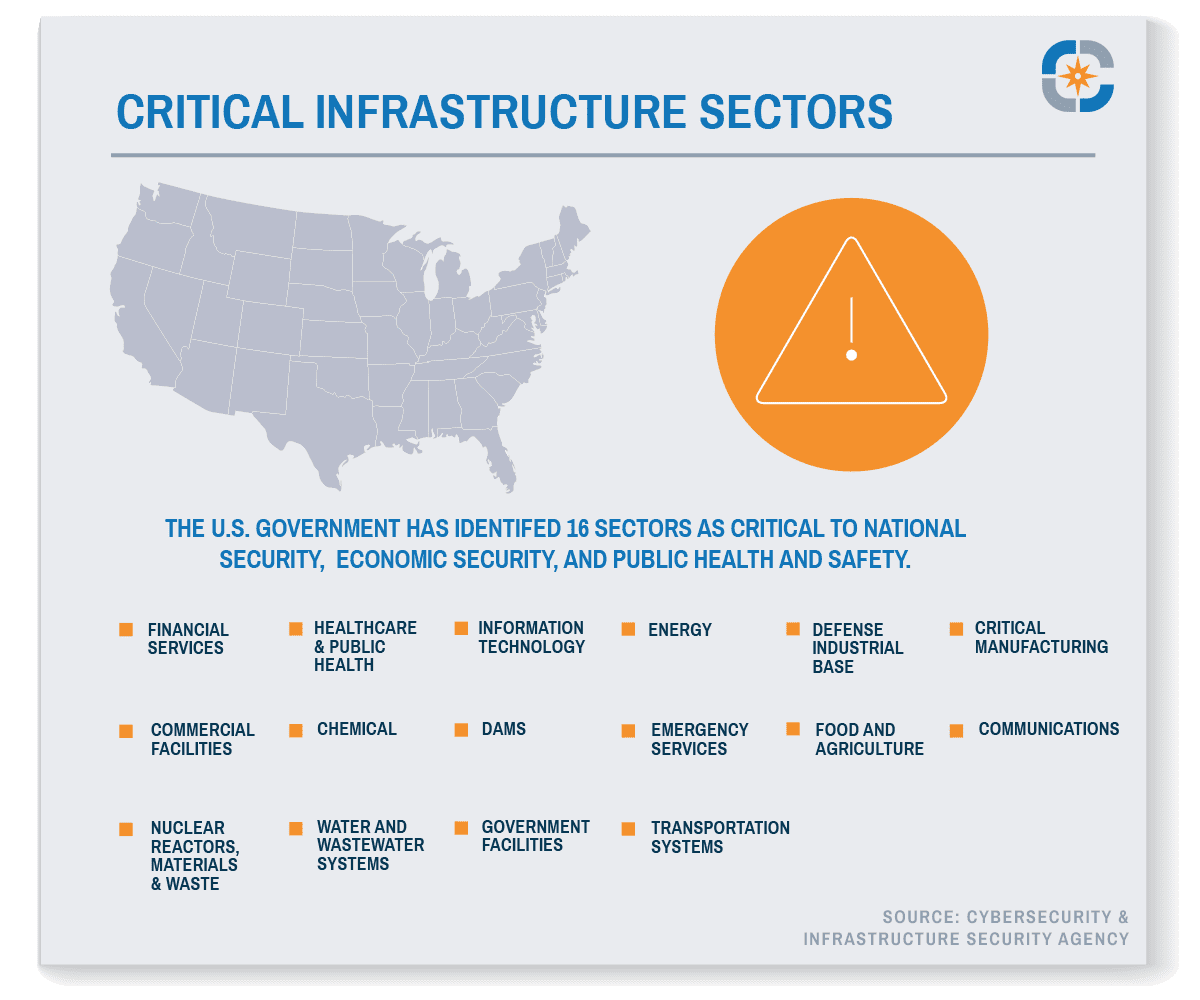
CISA identifies sixteen critical infrastructure sectors that provide essential services and are considered so vital that crippling cyber attacks would have a “debilitating effect on security, national economic security, national public health or safety, or any combination thereof.” Accordingly, these sectors are the target of the changes proposed within the Act.
What Are Considered Critical Infrastructure Sectors?
Organizations within these sectors will have 12-18 months after passage of the Strengthening American Cybersecurity Act to implement these and other policies and practices:
- Adopt Zero Trust, which is a shift away from the current practice of trusting all devices and traffic within a trusted network. Instead, zero trust applies security controls to ensure that employees have the appropriate access to the resources they need and that access is continuously assessed.
- Apply the Principle of Least Privilege in managing access to data. With this approach to information security, end-users are given the minimum levels of access possible, and access to higher levels of access is reviewed regularly.
- Execute improved mobile security standards and enhanced mobile device management (MDM). Implementing MDM allows IT departments to monitor, manage, and secure employees’ mobile devices that contain or access company assets.
- Identify and strengthen protections for systems likely to be targeted by ransomware. In addition, prepare for potential breaches by having an incident response plan and practice implementing it with tabletop exercises.
Reach out to our security experts to learn how your organization can get a jump on protecting your business from cyber threats and comply with all current and future requirements. Coretelligent offers robust multi-layered cybersecurity solutions to keep your organization secure and compliant. With over 16+ years of experience helping clients navigate IT compliance regulations and strengthening their cybersecurity programs, we can help your firm understand and meet its regulatory requirements.