Are you utilizing a multi-layered security solution? In today’s escalating environment, it is not enough to just have a cybersecurity solution, instead, your company needs a robust multilayered security solution that includes multiple checks and protections against intrusions.
[ez-toc]

Multi-Layered Security: How to Improve Your Cybersecurity Strategy
Cyber attacks are increasing at an alarming rate. In fact, global cyber attacks were up by 38% in 2022 over the previous year–and this trend doesn’t appear to be slowing down for 2023 either.
In light of this increase, are you putting yourself and your business at risk because of your deficient posture? The consequences of not being prepared for a data breach, ransomware, or other cyber incident are severe and include:
- Financial loss from shutdowns and restoration efforts
- Reputational damage
- Personal liability
- Fines and penalties from regulators
- Permanent loss of proprietary data
- Exposure of confidential and proprietary data
- Costly lawsuits from clients, employees, and others impacted by data breaches or loss of productivity from stoppages
- The complete failure and dissolution of your company
In evaluating your current posture, it is important to ask yourself the following questions:
- When was your company’s last vulnerability assessment?
- Have you made the recommended improvements?
- Do you know how to address your security vulnerabilities?
- Could you defend your current strategy to investors and regulators if a breach occurred?
Defend Against Escalating Threats with Layered Security
The potential risk from a deficient or merely adequate cybersecurity posture are just too significant. The escalating cyber threat landscape requires a rigorous, dynamic, and proactive security strategy. The only way to truly protect your firm from cyber threats is with a robust cybersecurity position. The most secure approach is utilizing multi-layered security protection, often referred to as defense-in-depth. Without this method, your company is an easy target for cybercriminals, and it could be considered negligent in the event of a cybersecurity incident.
To provide some context—your lax security approach is just as negligent as leaving your front door wide open and announcing to the world that you are out of town for the week.
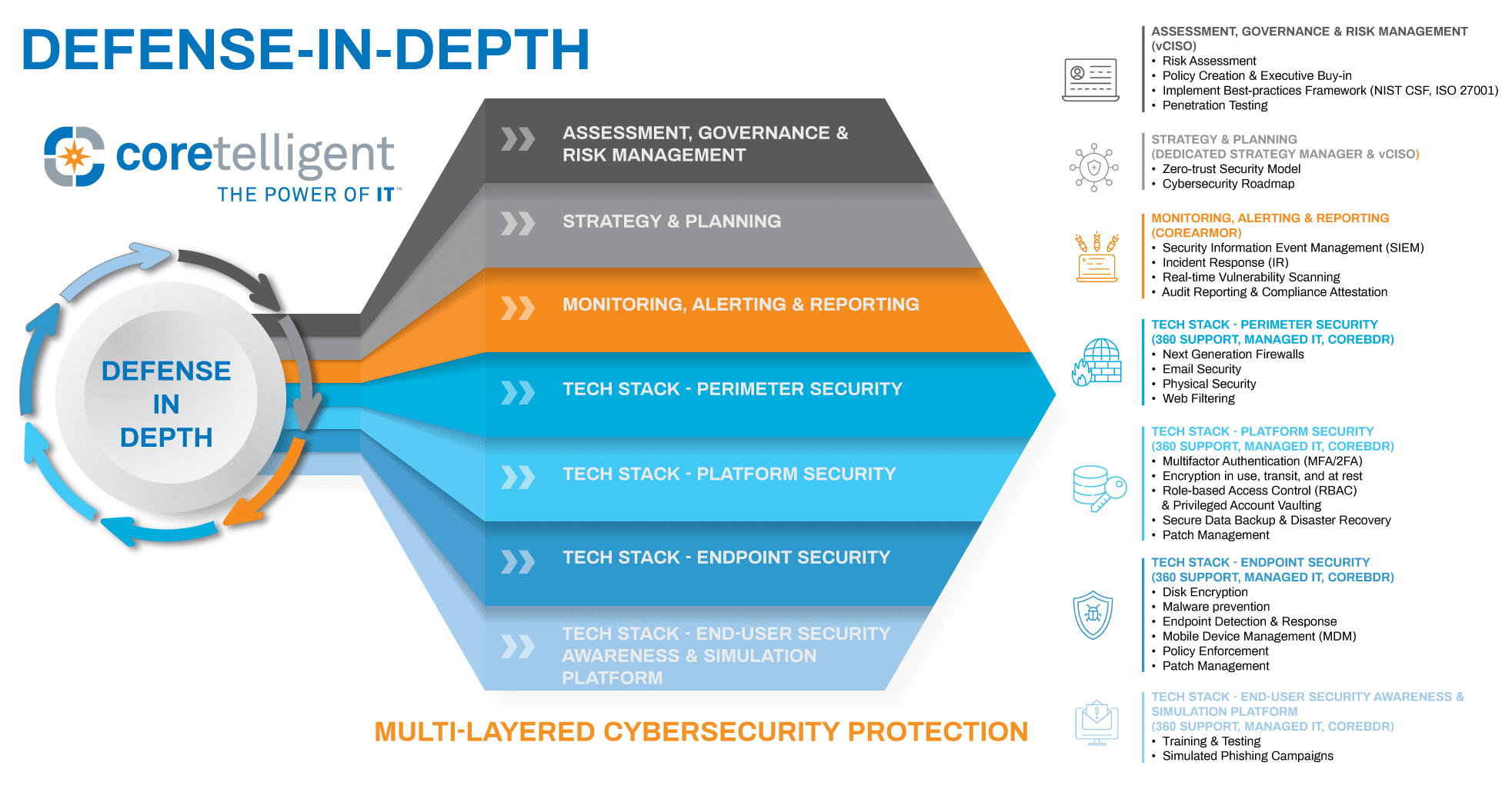
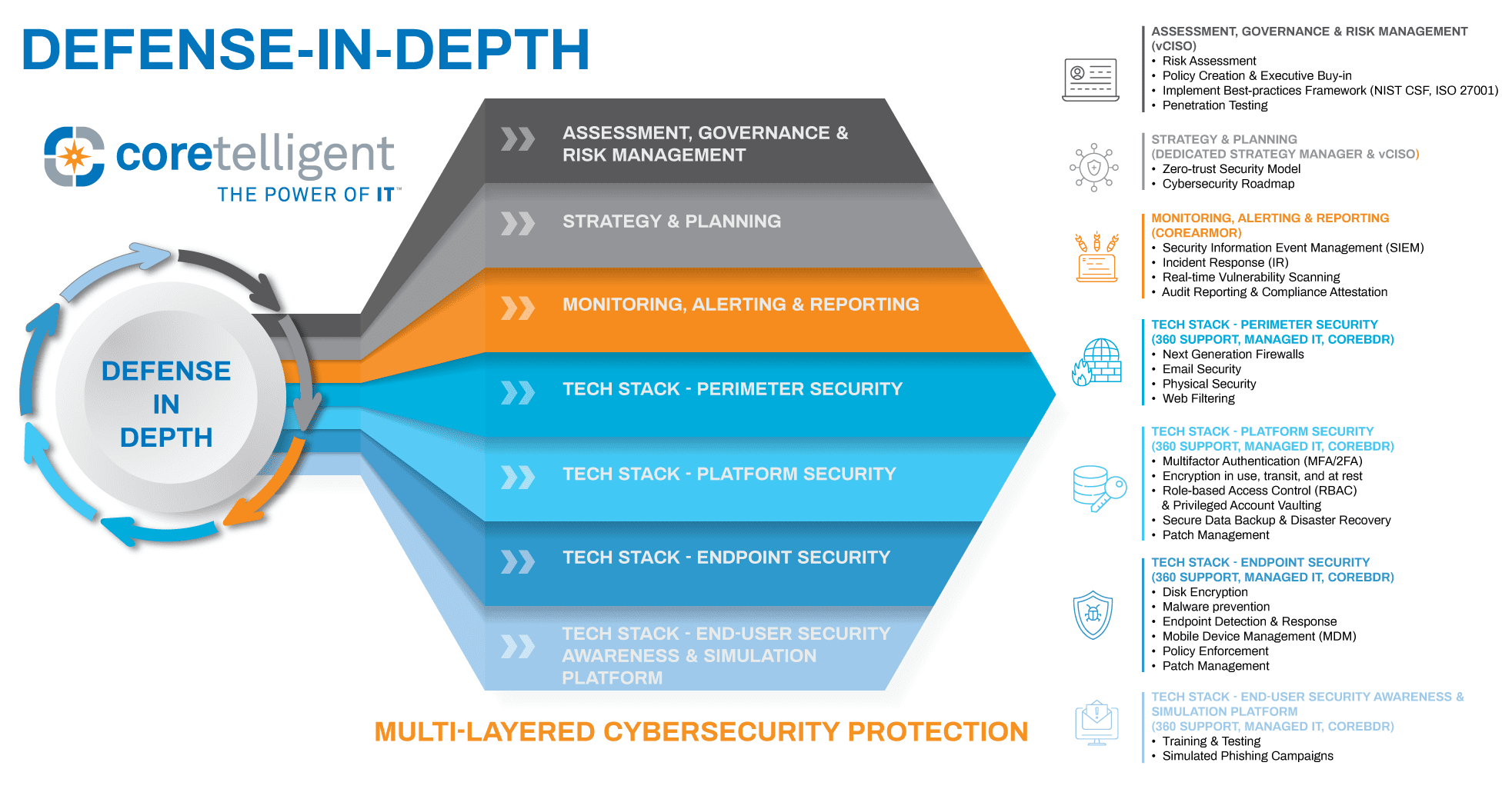
This infographic demonstrates the multilayered approach to security, specific best practices, and their associated Coretelligent solutions.
What Does Layered Cybersecurity Encompass?
Defense-in-depth is a system of overlapping security layers that range from easy-to-implement controls to complex security tools. These layers are designed to create an interlocking barrier, not unlike the security system at your home, which might include a door with a deadbolt, motion-detection lights, security cameras, and an alarm system that act as overlapping protections designed to safeguard your home. These individual protections combine to work as a system that is continuously protecting your home. Multilayered cybersecurity operates in the same manner. And just like your home security defends on two fronts—as a deterrent to criminals and as a barrier for any criminals foolish enough to attempt to break in—a strong cybersecurity posture defends on two fronts.
Our defense-in-depth infographic highlights the cybersecurity best practices that Coretelligent employs, including next-generation firewalls, endpoint detection and response, patch management and security updates, access management policies, advanced spam filtering, and more.
Evaluate Your Current Cybersecurity Solution
Looking to evaluate your organization’s current security coverage? Use our Cybersecurity Evaluation Checklist to help you appraise your firm’s cybersecurity readiness. This checklist is a jumping-off point to help your enterprise determine its ability to mitigate the risk of cyberattacks before it is too late.
After completing the checklist, reach out for questions about how Coretelligent can help to strengthen your cybersecurity. Learn more about what we offer, including cloud-based solutions, backup and business continuity services, IT planning and strategy, compliance solutions, and more here.