
Hedge funds, private equity companies, venture capital, and other financial services firms are prime targets for cyber criminals seeking to compromise data-rich institutions. Additionally, as keepers of valuable personal identifiable information (PII) and propriety data, the financial services sector is subject to increasing regulatory requirements as the cybersecurity threat landscape expands.
While financial firms have been highly motivated to make significant investments in cyber security, the need for risk management is only deepening from persistent threats. The Robinhood data breach is a recent reminder of the danger and the ease with which threat actors can gain access to networks. With over seven million customers affected, the Robinhood breach is the largest in history.
According to representatives from Robinhood, the cyber attack, which began with a social engineering exploit, has been contained and did not include social security numbers or account details. But what about the next time? What if the PII from over seven million customers found its way for sale on the dark web? The cascading consequences are staggering to contemplate.
“Financial services companies are incredibly popular targets because there are always new customers feeding the demand for personal and financial data to sell or use as leverage,” shares Chris Messer, CTO at Coretelligent. “Whether criminals are targeting your customers’ data to directly exploit, sell on the Dark Web, or to hold for ransom, the potential fallout for impacted clients and the financial and reputational risk to your business is extreme.”
There are more than a few emerging cyber threats that have security teams on edge. For example, the development of AI that can write better spearphishing emails than humans has staggering implications considering how many data breaches begin as phishing attacks. And don’t forget that phishing attacks are up by 22% in 2021.
In addition, AI-powered malware is a concern since it can target particular endpoints, making it more effective and profitable for hackers to cripple critical infrastructure and steal data with disruptive attacks. Finally, smishing incidents (like phishing, but via SMS) are also likely to increase in severity as attackers capitalize on a workforce that is increasingly doing business via their smartphones.
Multi-layered Approach to Information Security for Financial Service Organizations
Since businesses within the financial services industry are already required to have certain protections in place, it’s tempting to think that your organization is secure. But, unfortunately, between the increase in frequency and the changing nature of attacks—combined with the ever-changing compliance response—your cybersecurity implementation is not one-and-done. Instead, to keep up, a robust cybersecurity posture requires constant monitoring, continuing education of employees, periodic vulnerability assessments, regular penetration testing, and expert threat intelligence.
Coretelligent recommends implementing overlapping layers of security called defense-in-depth to protect your organization fully from ransomware attacks and other cyber incidents. These individual layers should include everything from easy-to-implement practices to complex security tools to defend your financial services organization. This defense-in-depth infographic highlights the cybersecurity strategy and best practices that Coretelligent employs for continuous multi-layered protection. These include next-generation firewalls, endpoint security, patch management and security updates, access management policies, advanced spam filtering, and much more.
Coretelligent’s Multi-layered Cybersecurity Solution
Are you looking to evaluate your organization’s current security coverage? Use our Cybersecurity Evaluation Checklist to help assess your firm’s cybersecurity readiness. This checklist is a jumping-off point to help your firm determine its current cyber risk exposure and readiness for critical event management.
After completing the checklist, reach out to learn more about how Coretelligent can help to strengthen your cybersecurity posture now and into the future.

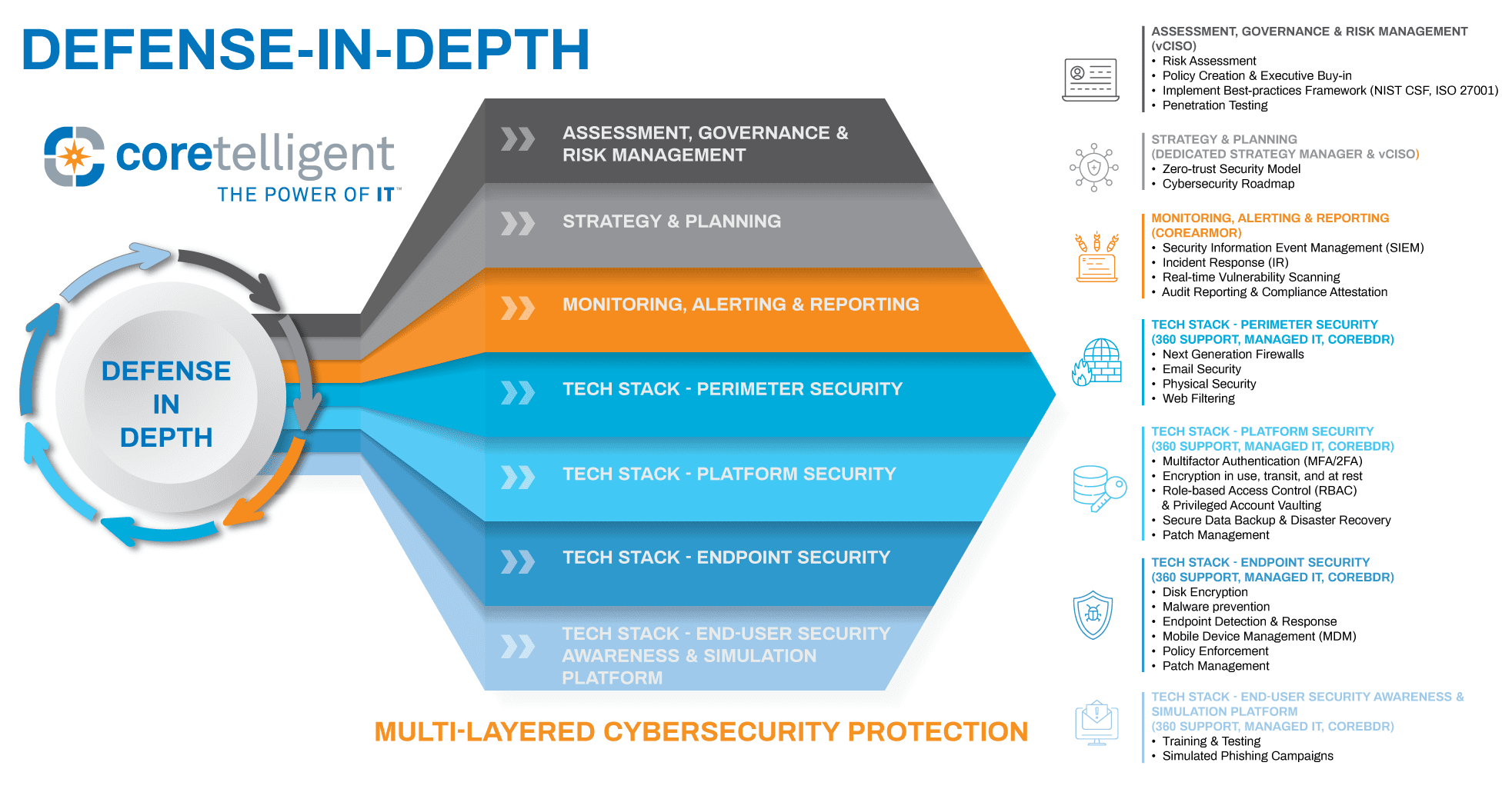
 Reducing your organization’s risk from cyber threats requires a holistic approach. Cybersecurity should be integrated across all divisions and at all levels. Cybercriminals do not recognize your internal organization or care about job titles but seek to exploit any weaknesses they discover.
Reducing your organization’s risk from cyber threats requires a holistic approach. Cybersecurity should be integrated across all divisions and at all levels. Cybercriminals do not recognize your internal organization or care about job titles but seek to exploit any weaknesses they discover.
