****Final Update 7/19/2021****
Coretelligent has re-enabled all external customer admin access this morning. Our engineering team is pleased to report that we are now 100% recovered and no further actions are needed at this time. We will continue to monitor the VSA environment over the coming days/weeks, and will also provide any additional postmortem information shared by Kaseya.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all measures we put in place were strictly precautionary in nature. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Friday Afternoon Update 7/16/2021****
Coretelligent engineering teams have been working around the clock, and we are pleased to announce all client workstations are now reactivated (ahead of schedule). At this time, we are planning to reconvene our engineer teams Monday morning and begin the process of re-enabling client access. We will send out messaging VIA email and here on our blog once all is complete on Monday.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Thursday Evening Update 7/15/2021****
We are pleased to announce that we will have full restoration of Kaseya VSA services to normal operations on Monday, 7/19 by 10am EST. This will include scoped client admin access for any technical resources.
At this time, all customer servers are back online with full monitoring, remote access, and automation capability for our teams as we previously communicated. In addition, regularly scheduled maintenance activities (patching, reboots, etc.) will resume based on existing schedules within the system.
For the remainder of today and Friday, we are bringing all remaining client workstation agents back online in a staggered fashion. We expect these to be fully online by close of business on Friday, 7/16, but we want to allow the weekend for the system to fully catch up and process all these agents as they have been offline for an extended period of time.
As a follow-up to the completion of our Kaseya VSA service restoration, we will be publishing a full breakdown of this incident from our CTO, Christopher Messer, here on our blog. We thank you for your patience during this time. The security and integrity of our customers continues to be the number one priority for our team. We feel that we have evaluated and implemented all reasonable controls to keep both our VSA platform as well as our customer environments secure.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Wednesday Evening Update 7/14/2021****
At this time we have brought all Coretelligent internal devices (servers & workstations) and all customer servers back online in Kaseya VSA and are monitoring overnight. Tomorrow we will begin bringing customer workstations back online, with our estimated goal of full-service restoration by Monday, 7/19.
At the moment, all access to Kaseya is restricted to Coretelligent employees on our local network(s) only. Global external access and customer admin logins to Kaseya remain disabled at this time. We plan to enable these items as the final step in the service restoration process.
We will continue to update you as we have additional information available via email and here on our Blog.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact us via 1-855-841-5888.
****Wednesday Afternoon Update 7/14/2021****
Coretelligent successfully applied the Kaseya VSA patch and all necessary config & security recommendations to our servers yesterday afternoon. We are continuing to slowly bring server agents online to minimize the performance impact. Workstations will be brought online after all critical servers are restored & tested. We are continuing to monitor security and performance metrics and will provide an update at end of day today.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Tuesday Evening Update 7/13/2021****
Coretelligent has successfully applied the Kaseya VSA patch to our servers this afternoon. We are now finalizing security lockdown efforts and service testing and validation with our internal servers before bringing services and external access online for customers.
We are continuing these efforts into the evening and will provide another update Wednesday morning on the overall restoration and testing status.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Tuesday Morning Update 7/13/2021****
Coretelligent engineering teams met this morning and reviewed Kaseya’s on-premise VSA patch details and general feedback & status to date. We have not heard of any major reported issues with the patch, and have commenced our Kaseya patching and restoration efforts. We expect this to run all day and will keep you informed in our evening update.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Monday Evening Update 7/12/2021****
The Kaseya VSA SaaS platform has been brought back online successfully and has been operational since Sunday. There was unplanned maintenance was performed across the entire Kaseya SaaS farm today, between 12:00 PM to 2:00 PM. With a large number of users coming back online in a short window, they were made aware of some performance issues. Kaseya made some configuration changes to address the issues during this downtime and needed to restart the servers for these to take effect and improve performance. The unplanned maintenance across the VSA SaaS infrastructure has been completed and all instances are now live.
Coretelligent engineering teams met this afternoon and reviewed the on-premise VSA patch details and general feedback & status to date. We have not heard of any major reported issues with the patch, however, we are opting to wait overnight to see if any additional feedback comes in from other Kaseya VSA customers that have applied the patch in their environment.
At this time, we are planning to reconvene our engineer teams at 10 AM EST on Tuesday (tomorrow), and barring any reported issues, will begin patching and configuration efforts to bring our VSA server back online. We expect this will be a phased process, and to avoid performance issues, we will bring individual clients & endpoints back online in a staggered manner. In addition, we will not enable client admin access until we have finished testing and validating the new security measures.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Monday Morning Update 7/12/2021****
Kaseya released the patch to VSA On-Premises customers and began deploying to their VSA SaaS Infrastructure before yesterday’s 4:00 PM target. The restoration of services is now complete, with 100% of their SaaS customers live as of 3:30 AM US EDT. Kaseya’s support teams continue to work with VSA On-Premises customers who have requested assistance with the patch. Coretelligent will be reviewing the patch status later today and then releasing our own timeline for restoration.
Please continue to be assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Sunday Morning Update 7/11/2021****
Coretelligent’s internal team has reviewed Kaseya’s startup runbook and security recommendations, and are ready for the patch release, which is still slated for Today at 4 PM EDT. As stated in earlier communications, Coretelligent will be reviewing the patch upon release, but will not be applying it immediately. We will wait 24 hours at minimum to ensure things are stable & fully validated before beginning to restore our VSA server infrastructure on either Monday or Tuesday.
Please continue to be assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Saturday Evening Update 7/10/2021****
Coretelligent’s internal team has reviewed Kaseya’s startup runbook and security recommendations, and are ready for the patch release, which is still slated for Sunday, July 11th at 4 PM EDT. Please continue to be assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Saturday Morning Update 7/10/2021****
Kaseya remains on track to release the VSA On-Premises Patch and begin deployment to their VSA SaaS Infrastructure on Sunday, July 11th at 4 PM EDT.
As previously communicated, spammers are using the news about the Kaseya Incident to send out fake email notifications that appear to be Kaseya updates. These are phishing emails that may contain malicious links and/or attachments. Spammers may also be making phone calls claiming to be a Kaseya Partner reaching out to help. To be clear, Kaseya IS NOT having any partners reach out – DO NOT respond to any phone calls claiming to be a Kaseya Partner.
Please continue to be assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Friday Evening Update 7/9/2021****
As previously communicated, spammers are using the news about the Kaseya Incident to send out fake email notifications that appear to be Kaseya updates. These are phishing emails that may contain malicious links and/or attachments. Spammers may also be making phone calls claiming to be a Kaseya Partner reaching out to help. To be clear, Kaseya IS NOT having any partners reach out – DO NOT respond to any phone calls claiming to be a Kaseya Partner.
Kaseya will be providing a video update from their Executive Vice President, Mike Sanders, later this evening with an update on the incident, their response, and release planned for this Sunday at 4PM US EDT. In the meantime, Coretelligent has run the Kaseya Compromise Detection Tool against our VSA servers and they came back clean as expected. We are ready for the upcoming patch release and return to production operations next week. Please continue to be assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Friday Morning Update 7/9/2021****
Please continue to be assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Unfortunately, Kaseya is reporting a number of spammers targeting the public with fake email notifications that appear to be Kaseya updates. These are phishing emails that may contain malicious links and/or attachments. Do not click on any links or download any attachments in emails claiming to be a Kaseya advisory coming from outlets you are not already familiar with. Official updates from Kaseya will no longer include attachments or links.
Kaseya has also released VSA On-Premise Hardening and Practice Guide as well as runbooks for the upcoming release. As communicated previously, the On-Premises Patch will be available and Kaseya will start the deployment to their VSA SaaS Infrastructure Sunday, July 11th at 4 PM EDT. Coretelligent will be reviewing the patch upon release, but will not be applying it immediately. We will wait 24 hours at minimum to ensure things are stable & fully validated before beginning to restore our VSA server infrastructure on either Monday or Tuesday.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Thursday Evening Update 7/8/2021****
Kaseya has announced the On-Premises Patch will be available and they will start the deployment to their VSA SaaS Infrastructure Sunday, July 11th at 4 PM EDT. Coretelligent will be reviewing the patch upon release, but will not be applying it immediately. We will wait 24 hours at minimum to ensure things are stable & fully validated before beginning to restore our VSA server infrastructure on either Monday or Tuesday.
Kaseya’s CTO will also begin providing technical updates, both written and video later this evening in addition to the regular progress updates we’ve been getting. Please be rest assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and this Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689.
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
Best,
Your Coretelligent Team
****Thursday Morning Update 7/8/2021****
Kaseya’s CEO, Fred Voccola, just posted a video update. In the update, he outlines a plan in which Kaseya has opted to hold the patch which will allow them the time to add additional security measures and protections, at the advice of various resources. The new estimated time for the patch release is Sunday afternoon.
Kaseya’s CTO will also begin providing technical updates, both written and video in addition to the regular progress updates we’ve been getting. Coretelligent continues to monitor the ongoing Kaseya situation and will provide regular updates as they become available.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email here, on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689. Kaseya’s CEO also recently released a helpful video that gives a great update as well as an overview of the situation: https://www.youtube.com/watch?v=XfAyutRfy2A
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Wednesday Evening Update 7/7/2021****
Kaseya is currently in the process of resetting the timelines for VSA SaaS and VSA On-Premises deployment. The current situation remains fluid at this point in time. We are awaiting a video update from Kaseya’s President which is said to provide additional clarity on the situation. Coretelligent continues to monitor the ongoing Kaseya situation and will provide regular updates as they become available.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689. Kaseya’s CEO also recently released a helpful video that gives a great update as well as an overview of the situation: https://www.youtube.com/watch?v=XfAyutRfy2A
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Wednesday Afternoon Update 7/7/2021****
Kaseya just announced that all On-Premise customers should expect a runbook of the changes to make to any On-Premises environment by 3 PM US EDT today so customers can prepare for the patch release. Updates will be made to the planned availability of the VSA On-Premises patch by 5 PM US EDT today. During the VSA SaaS deployment, an issue was discovered that has blocked the release. We are resolving the issue that is related to our SaaS infrastructure and we plan on beginning to restoring SaaS services no later than the evening of Thursday, July 8th US time. Please note that these times are however subject to change due to unforeseen circumstances. Coretelligent continues to monitor the ongoing Kaseya situation and will provide regular updates as they become available.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689. Kaseya’s CEO also recently released a helpful video that gives a great update as well as an overview of the situation: https://www.youtube.com/watch?v=XfAyutRfy2A
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Wednesday Morning Update 7/7/2021****
We will continue to push communications around Kaseya as they become available. Most recently, Kaseya has recently announced that an issue was discovered last night as they were trying to deploy the VSA update. This issue has in turn blocked the release. Kaseya’s R&D and Operations teams have worked through the night and will continue to do so until they have unblocked the release, with plans on giving another update on their progress this afternoon. Coretelligent continues to monitor the ongoing Kaseya situation and will provide regular updates as they become available.
We will update you as we have additional information available VIA email and this blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
To be clear, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Tuesday Afternoon Update 7/6/2021****
Coretelligent continues to monitor the ongoing Kaseya situation and will provide regular updates as they become available. Recently, Kaseya announced they are aiming to bring SaaS servers online July 6th between 4:00 PM EDT and 7:00 PM EDT. This delay was due to configuration change and enhanced security measures being put in place. They also announced On-Premises patch timeline is 24 hours (or less) from the restoration of SaaS services. They are continuing efforts to shrink this time frame as minimally possible.
It is important to note, once the On-Premises patch is released by Kaseya, Coretelligent will be reviewing and testing internally before applying to our systems, so there will be some additional delay before our services are brought back online.
As part of the overall VSA service restoration effort, Kaseya also announced several security measures to improve overall platform security.
The enhanced security measures that will be brought online are:
- 24/7 Independent SOC for every VSA with the ability to quarantine and isolate files and entire VSA servers.
- A complementary CDN with WAF for every VSA (Including on-premise that opt-in and wish to use it – details will be available in a KB later this afternoon).
- Customers who whitelist IPs will be required to need to whitelist additional IPs.
- A new KB article on the SOC, CDN, and Whitelisting details will be published later this afternoon and linked to this KB on the Kaseya website.
- Greatly reduces the attack surface of Kaseya VSA overall.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689. Kaseya’s CEO also recently released a helpful video that gives a great update as well as an overview of the situation: https://www.youtube.com/watch?v=XfAyutRfy2A
Once again, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Monday Afternoon Update 7/5/2021****
Currently, Kaseya is continuing its investigation and testing operations to develop a software patch for this vulnerability. Kaseya has informed us the next status update we receive from then will be between 5pm and 7pm EST tonight. We are continuing to monitor and will provide updates when available.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and here on our Blog. Additional updates via Kaseya can be found here:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
To be clear, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Sunday Evening Update 7/4/2021****
Currently, Kaseya is continuing its investigation and testing operations to develop a software patch for this vulnerability. We are expecting a patch release at some point tomorrow. Once we have the release from Kaseya, Coretelligent will begin to bring service back online. We are continuing to monitor and will provide updates when available.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and this Blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
To be clear, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Sunday Morning Update 7/4/2021****
Currently, Kaseya is continuing their investigation and testing operations to develop a software patch for this vulnerability. We are continuing to monitor and will provide updates when available.
In the interim, customers are protected via endpoint security software (SentinelOne, Webroot, etc.). All major vendors are updated and tracking to block the ransomware and infected files that were used in this attack. This will help provide additional protection and visibility until our Kaseya VSA platform is fully patched and brought back online.
For Coretelligent customers leveraging SentinelOne for endpoint security, they have created a short video demonstrating the SentinelOne agent protecting against the Kaseya attack. You may view the video here: https://assets.sentinelone.com/ransom/Kaseya.
Coretelligent customers leveraging Webroot are also protected, as Webroot has also added the appropriate information into their system to identify and block the elements used in this attack.
Our support team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and this Blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
To be clear, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
Best,
Your Coretelligent Team
****Saturday Evening Update 7/3/2021****
We are continuing to monitor the ongoing Kaseya situation.
Currently, Kaseya is still performing their investigation and testing operations. Our team continues to be available and is utilizing alternate methods to provide support for end-users. We will update you as we have additional information available VIA email and this blog. Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
To be clear, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary. If you have any questions, please contact Coretelligent at 1-855-841-5888.
****Saturday Morning Update 7/3/2021****
As you’re already aware per our email notice yesterday, there has been a security issue that has impacted other Managed Services Providers leveraging the Kaseya Remote Monitoring and Management (RMM) platform. Please be rest assured, no one at Coretelligent, nor any Coretelligent customers have been affected by this, but we will continue to monitor and update you on the situation.
The current guidance from Kaseya is to keep servers shutdown and await further instructions on when it will be safe to resume. There will then be a software patch required before normal operations can be restored. Currently, there is no ETA on this patch from Kaseya at the moment.
Coretelligent is continuing to monitor the situation and we will send out twice-daily email updates (AM and PM). We will also post any updates in this blog as they are available.
Additional updates via Kaseya can be found here: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
A comprehensive update is in progress and will be published later this morning (EDT). This communication will include prescriptive information on:
- The external authorities (FBI, Incident Response Experts) that we have engaged and how we are leveraging them for assistance;
- How our customers can engage Kaseya for assistance and what we can do to help;
- How to determine whether customers have been compromised;
- Status updates from R&D on the progress of the patch for on-premises users;
- The plan to bring our SaaS and on-premises customers back online;
- A detailed description of the Security Incident process and current status;
- A schedule for communications updates;
- Other important information about the recovery process.
Ongoing updates will be provided every 3-4 hours or more often based on breaking details.
Our team continues to be available and is utilizing alternate methods to provide support for end-users. To be clear, Coretelligent, nor any of our customers, have been affected by this security issue, all of these measures are strictly precautionary.
If you have any questions, please contact Coretelligent at: 1-855-841-5888.

 Similarly to 2020, when many businesses shifted to
Similarly to 2020, when many businesses shifted to 
 As you read or listen to the news about the increase in cybercrime—or as you evaluate your organization’s cybersecurity posture–you may come across some unfamiliar terminology. While you do not have to become a cybersecurity expert, having at least a basic knowledge of cybersecurity terms can be an advantage in today’s cybersecurity ecosystem.
As you read or listen to the news about the increase in cybercrime—or as you evaluate your organization’s cybersecurity posture–you may come across some unfamiliar terminology. While you do not have to become a cybersecurity expert, having at least a basic knowledge of cybersecurity terms can be an advantage in today’s cybersecurity ecosystem.


 The Financial Industry Regulatory Authority (FINRA)
The Financial Industry Regulatory Authority (FINRA) 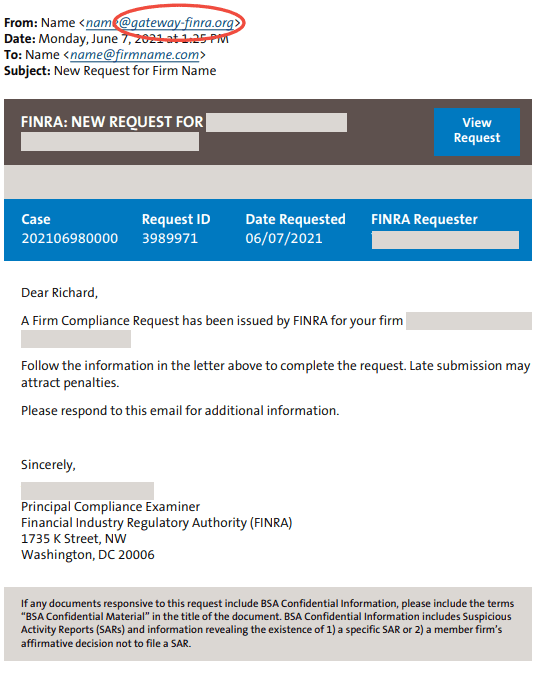

 In 2020 ransomware victims paid over $350 million in ransom to cybercriminals—a 311% increase over the prior year—according to a 2021 report from the
In 2020 ransomware victims paid over $350 million in ransom to cybercriminals—a 311% increase over the prior year—according to a 2021 report from the