 The life sciences industry is experiencing a period of rapid growth. Not only does the sector produce life-saving and life-enhancing treatments, but it is fueling investment across the globe. For example, 78 startups went public in 2020 in the biotech sphere, representing a 77% increase from the previous year. Additionally, the first half of 2021 saw already seen 62 biopharma companies progress to IPO status. With the increased demand for innovative drugs, medical devices, and other therapies in the wake of the ongoing COVID-19 pandemic and vaccine development, various trends within the industry (like changes to clinical trials), and increased levels of investment, 2022 is shaping up to be a big year for the sector.
The life sciences industry is experiencing a period of rapid growth. Not only does the sector produce life-saving and life-enhancing treatments, but it is fueling investment across the globe. For example, 78 startups went public in 2020 in the biotech sphere, representing a 77% increase from the previous year. Additionally, the first half of 2021 saw already seen 62 biopharma companies progress to IPO status. With the increased demand for innovative drugs, medical devices, and other therapies in the wake of the ongoing COVID-19 pandemic and vaccine development, various trends within the industry (like changes to clinical trials), and increased levels of investment, 2022 is shaping up to be a big year for the sector.
Innovation is the driver of the current expansion within the life sciences market. However, the key to maximizing this ROI, or Return on Innovation, requires that business and technology synchronize. This imperative calls for a carefully planned IT roadmap that enables companies to achieve a competitive advantage and improve business outcomes throughout the development, startup, growth, and expansion stages.
To help executives better understand the timeline, Coretelligent has developed a chart outlining the technology and business needs of the life sciences ecosystem throughout their life cycle. Download our datasheet Innovation is Where Business & Technology Intersect outlining how to plan your company’s IT strategy as you move through funding phases.
To dive deeper, download our data sheet → Innovation is Where Business & Technology Intersect.
In an earlier post, we shared some of the IT challenges faced by early-stage life sciences organizations. With this post, let’s take a deeper look at later-stage companies and what their IT strategy should be focused on as they scale.
What are the main IT priorities of life science firms as they move into their growth and expansion stages?
→ Employ technology for data management
As biotech, biopharma, and other life science enterprises grow, managing data increases in scale and complexity. As a result, cloud-based solutions and SaaS applications must align to ensure that enterprise data is available, usable, consistent, reliable, and secure. Employing the right technology solutions, including cloud-based services, backup and recovery, and others that store, manage, and protect data are critical at this stage.
→ Leverage technology to drive innovation
Not only has innovation come to the life sciences space, but it’s also bringing emerging technological trends with it. Advances in Artificial Intelligence (AI), Robotic Process Automation (RBA), Machine Learning (ML), Cloud/Big Data, and other developing technologies are evolving as disrupters to the sector. Successful life science companies will envision how to capitalize on these tools.
→ Optimize technology to grow operations
Even as innovative technology trends shift the landscape, IT becomes more integral to the core business operations as companies scale. While some may be using a managed IT model, most companies likely employ co-managed solutions during the later stages. A co-managed service provider empowers internal IT staff to drive technology delivery at scale and focus on strategic priorities. A technology partner can lighten the load by fulfilling tech support, plug critical skill gaps, and complement in-house capabilities with specialized technology services.
→ Utilize technology to ensure security and compliance
As a life science firm grows, compliance requirements increase in size and scope. At the same time, these companies have become more attractive targets for cybercriminals. As a result, life science firms must prioritize implementing robust cybersecurity tools and compliance processes to keep pace with evolving regulations while protecting sensitive data from bad actors.
Related Content → GxP and FDA 21 CFR Part 11 Compliance with Egnyte for Life Sciences.
Developing IT Growth Strategy for the Life Sciences Industry
The life sciences industry is booming, and the future looks even brighter. But the key to success involves more than just innovation—effective growth also depends on how well your life sciences company can leverage IT capabilities throughout your life cycle. In building out an effective IT strategy for startups, begin by understanding where your organization stands today, followed by preparing for those IT areas that will require digital transformation. Furthermore, leveraging new technologies like AI, RPA, ML, and Big Data, can help accelerate your progress and open up new opportunities in the journey towards achieving your goals.
To sum up, you need to understand what’s possible before embarking on any journey. By taking stock of current practices, planning ahead, prioritizing initiatives based on pain points, incorporating new technologies, and teaming up with a technology partner, you’ll be well-positioned to meet future growth. Coretelligent is an industry leader with extensive experience in the life sciences sector. To learn more about how Coretelligent can help your company successfully scale so that growth doesn’t stifle innovation, talk to one of our technology experts today.


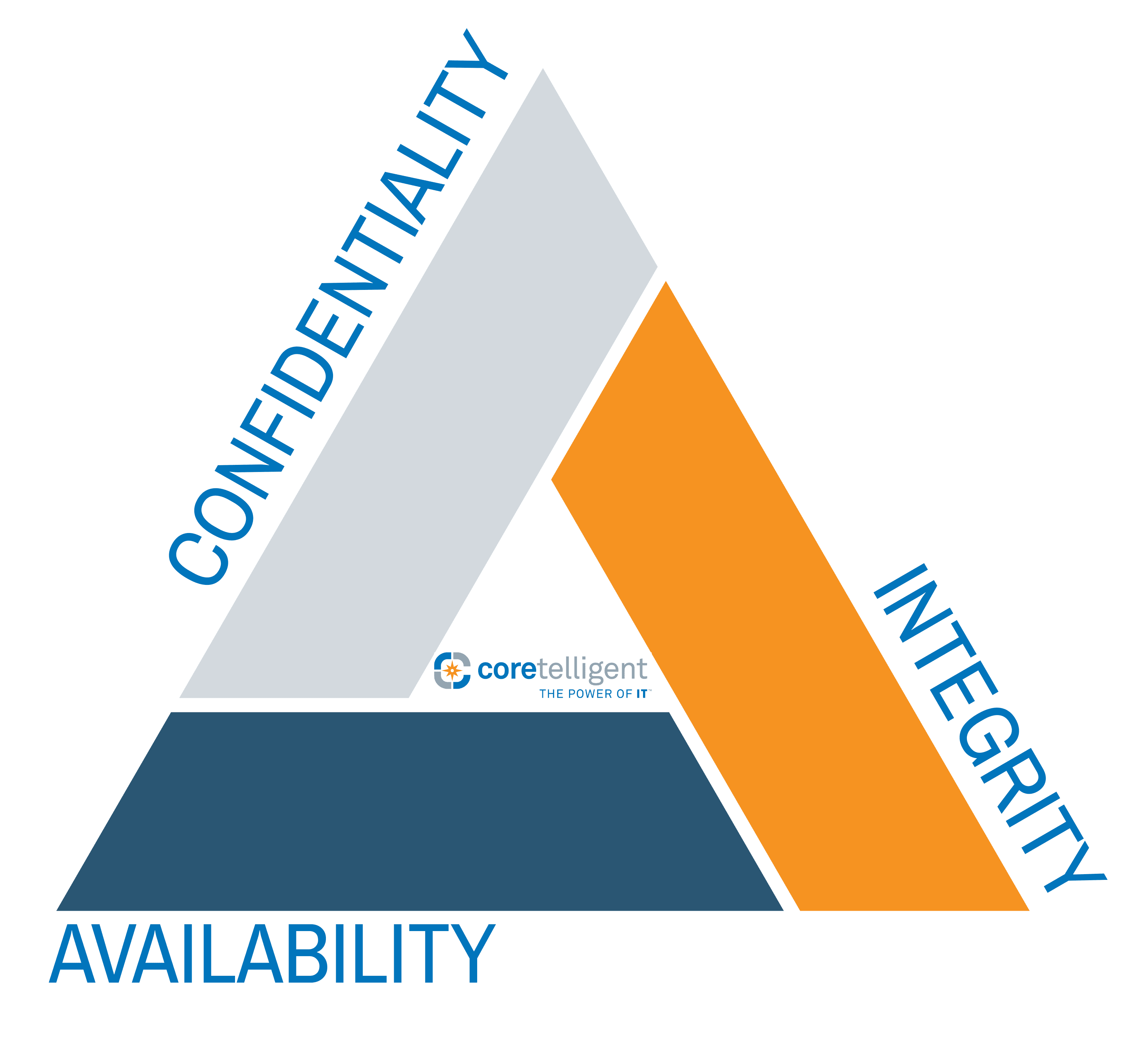



 Improving the operation of your business often starts with consolidation: creating a more cohesive structure that eliminates redundancy and slashes inefficiencies throughout the organization. Business leaders have been focused in this direction for generations, often looking for the smallest advantages that will allow them to outpace the competition. With the renewed focus on cybersecurity, it’s not unusual for businesses to focus more on protecting the security of their organization than attempting to improve operational excellence. What you may not realize is that some of the same initiatives that will help smooth operational hurdles can also provide added levels of cybersecurity. What can be difficult is finding the spaces where you can bring these goals into alignment and create a comprehensive strategy that addresses the holistic needs of the organization and provide proactive cybersecurity support.
Improving the operation of your business often starts with consolidation: creating a more cohesive structure that eliminates redundancy and slashes inefficiencies throughout the organization. Business leaders have been focused in this direction for generations, often looking for the smallest advantages that will allow them to outpace the competition. With the renewed focus on cybersecurity, it’s not unusual for businesses to focus more on protecting the security of their organization than attempting to improve operational excellence. What you may not realize is that some of the same initiatives that will help smooth operational hurdles can also provide added levels of cybersecurity. What can be difficult is finding the spaces where you can bring these goals into alignment and create a comprehensive strategy that addresses the holistic needs of the organization and provide proactive cybersecurity support.
 Even with all of the available technology solutions, one of the biggest challenges you will continue to hear from technical teams is lack of time. Everything from upgrading current platforms to researching new solutions requires dedicated focus, and the ability to shut out all by-the-minute frustrations and do the work required to move your organization into the future. It’s not surprising to find that many business professionals feel as though they are being shut down by IT teams and attempt to “go rogue” — something that would be less likely to happen if IT teams are able to meet their needs more quickly. Outsourced IT solutions is a cost-effective and practical way to solve these challenges.
Even with all of the available technology solutions, one of the biggest challenges you will continue to hear from technical teams is lack of time. Everything from upgrading current platforms to researching new solutions requires dedicated focus, and the ability to shut out all by-the-minute frustrations and do the work required to move your organization into the future. It’s not surprising to find that many business professionals feel as though they are being shut down by IT teams and attempt to “go rogue” — something that would be less likely to happen if IT teams are able to meet their needs more quickly. Outsourced IT solutions is a cost-effective and practical way to solve these challenges.
 Cyberattacks and data breaches are omnipresent in the headlines, and this trend shows no sign of slowing down. In fact, for a third consecutive year, instances of
Cyberattacks and data breaches are omnipresent in the headlines, and this trend shows no sign of slowing down. In fact, for a third consecutive year, instances of 
 This is the debut post from Coretelligent’s Chief Information Security Officer (CISO), Jason Martino. Jason will be regularly sharing his thoughts about information security on the Coretelligent blog.
This is the debut post from Coretelligent’s Chief Information Security Officer (CISO), Jason Martino. Jason will be regularly sharing his thoughts about information security on the Coretelligent blog.  About Jason
About Jason


